Data misuse is the use of data in an unintended manner. The terms and conditions of a company typically stipulate how data should be used. But either due to lack of knowledge, ignorance, or malicious intent, company data is misused by, members of the organization and shared with third parties and even family members.
The most common reasons for data misuse are lack of awareness, blackmail, personal gain-mostly in terms of money or personal edge, or use of trade secrets to start a business. In business, this can mean loss of revenues and reputation.
When it comes to prevention, restriction of access to data should be a priority. Ethyca entitlements management service can create a hierarchy of permission for your company. You will be able to grant or revoke access across all platforms and networked components.
Encryption
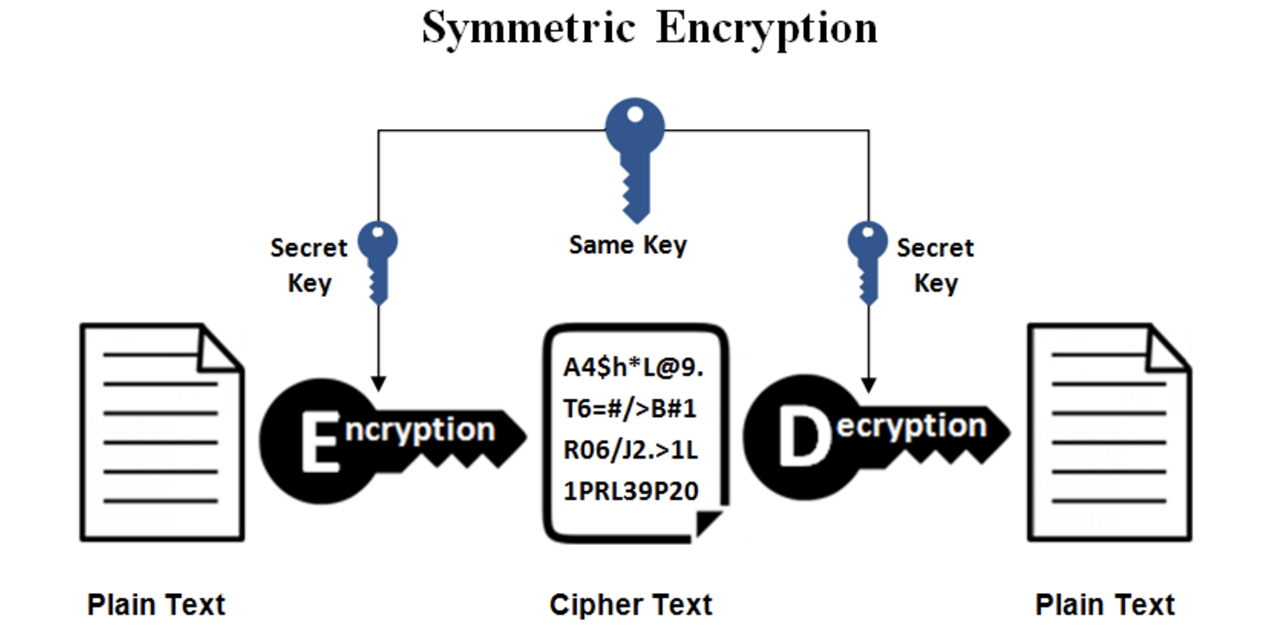
This refers to the process in which raw data or plain text is scrambled into “ciphertext” so that it remains hidden from unauthorized users. Only those who are within the network, organization, or database possess the decryption key and can read it. This prevents intrusion from outsiders and private communication between client apps and servers. Even if an unauthorized entity gains access, they cannot read the text.
Data use is therefore restricted to those within the database. In this case, misuse is considerably manageable.
Managing data access

Data entry points offer a prospect of misuse. Database networks should manage the type of data being entrusted to various members. Employees may bump into highly confidential or sensitive data that they aren’t supposed to see. It’s important to verify the user’s identity.
An identity crisis mostly occurs in shared devices among colleagues. However, there are methods like two-factor authentication that eliminates this dilemma. For example, in two-factor authentication one is asked to input more than the password.
Monitoring user actions

Once you manage data entry points, you will need to monitor the kind of activity that happens after. This is the best method to prevent data misuse. The last thing you want is an inside job. You need to know what exactly has been done with the accessed data. Activity logs involve how data was used, whether it was read, pasted, or edited, when and by whom. This made possible by use of modern user activity monitoring solutions.
Instead of collecting activity logs, logging action is scrutinized with a keen eye by continuous observation with recordings of each operation. Sessions can be assessed within seconds and judged if there was any form of malicious intent.
Staying informed
Data security personnel needs to have constant feedback on what is going on in the network. Activity records and logs of thousands of employees can be tiresome activities for any human being. That’s why alert and notification functionality is a must. Any event is within the awareness of the security personnel. These notifications can include connecting a new USB device, report from an AI module on how long an employee is working on sensitive data.
Notification of any illegal or suspicious activity demands immediate and effective action to prevent data misuse or breach. All this should be done in real time. A customized rule-based system offers a fluid form of communication within the network.